4/30/10
Local Mac User to an AD User
(Other versions may differ)
Here is the scenario. Mac User has a local account and his “Short Name” is muser and his Home Directory is muser as well. The problem is that when we join this computer to Active Directory, and Mac User logs on, it will want to make a Home Directory for him with the name of muser.
So, we have to delete the local Mac User user, but preserve his Home Directory. Then we have to move it to the network Mac User user and assign the correct permissions.
Step One. Join computer to Active Directory. There are many guides out there on how to do this. Official Apple docs http://docs.info.apple.com/article.html?path=ServerAdmin/10.5/en/c7od44.html
Step Two. Log in as a different Local Admin account than the one you want to change. If one doesn’t exist, create one. If possible, back up the users Home Directory before proceeding just to be safe. Now go into System Preferences and then Accounts. Now, unlock things and then select “Mac User”. Now click the “-“ to remove him. You want to select the middle option on the next screen which is “Do not change the home folder (The home folder remains in the Users folder.)” Click “OK” and then log out.
Step Three. Click on the “Other” option at the Login screen and log in as the network Mac User account to create his profile. When you are asked to create a mobile account, click the “Create Now” button. Log out and log back in as the local Admin account you were using in step Two.
Step Four. Open the terminal and enter the following:
sudo rm –r /Users/muser
sudo mv /Users/”muser (Deleted)” /Users/muser
sudo chown –R muser /Users/muser
If this user should be a local admin, click the “Allow user to administer this computer” box under his profile. Log out.
Step Five. Log in as the network user and all your programs, data, and settings should be moved over to the new profile.
Step Six. You may have to fix the keychain. If there is an issue with getting prompted for the keychain password, go into utilities and then click on Keychain Access. Right click on the “Login” keychain and at the bottom of the list you will see “Change Password…” Once you click it, you will be prompted for the old password and then enter a new password.
Done. Now the Mac user will be able to change their network password, be prompted when it is about to change, and most importantly, be required to use one. Your mileage may very so test out these steps in the lab first.
4/14/10
How to deploy an Aruba Remote Access Point (RAP) Part 2
So in part one I gave the back-story so now it’s onto getting this going. I’m using Aruba OS 5 on an Aruba 650 Controller with AP-61 access points. Your mileage may very.
If your running Aruba OS 5, you don’t need any RAP licenses with is great. Not so great if you bought them before OS 5 came out though. Good news is, they get turned into AP licenses when you upgrade to OS 5.
One more thing, since you will be deploying these access points in RAP mode, you won’t have some features. You won’t be able to tell how many people are on your system from that location so I wouldn’t go more than a few AP’s. You can’t blacklist someone. I don’t think you can do heat maps (I’ll have to try this though). Also, because we are setting these AP’s up in bridge mode, they will use the local DHCP server and if you have more than one AP, they need to be on the same Vlan. You will also have to take care of any extra security by using a local ACL on a switch or router.
Step One, log into your controller by going to https://aruba-master just to check that you have your DNS set up properly.
Step Two, navigate to Configuration –> Wireless –> AP Configuration. 
Create a new AP Group by clicking on the New button. I’m giving it the name “RAP”. Click “Add” and then “Edit”. ![]()
Now, you will have to drill down to Wireless LAN –> Virtaul AP and create a new Virtual AP. Click the drop down and select –NEW – at the bottom of the list. Then, give it a name. I’m going to use “test-vap_prof” which is one I use for testing. After you click “Add”, you have to select the AAA profile and the SSID profile. You can use the same ones you used for your campus profile since you won’t change them. I’m going to use some test ones though. After you select the ones you want to use, click “Apply” in the lower right. ![]() Now, drill down one level to the Virtual AP you just set up. The only setting you want to change is the “Forward mode” from “Tunnel” to “Bridge” and click “Apply”
Now, drill down one level to the Virtual AP you just set up. The only setting you want to change is the “Forward mode” from “Tunnel” to “Bridge” and click “Apply”
Step Three, Set up the VPN. This is the step that kept throwing me off. Why do I need to set up a VPN connection between the AP and the controller if I’m on the local LAN? That’s just the way it is. If you don’t, the AP will never become a RAP on your AP Installation screen. This step is also what makes the controller push out the new RAP firmware to the AP. Navigate to Configuration –> Advanced Services –> VPN Services.
So, now that your on the VPN Services screen, You need to add an Address Pool. Just click “Add” under Address Pools. These addresses don’t have to be routable on your network. It’s probably better to pick ones that aren’t so you don’t have any confusion too. 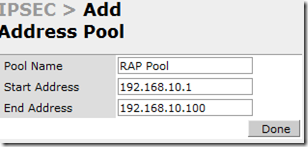
Click “Done”.
Now you need to set up the IKE Secret. Under IKE Shared Secrets, click “Add”. You can keep the Subnet and Subnet Mask as quad zero (0.0.0.0) if you don’t have any other PSK’s. Enter the IKE and then confirm it. 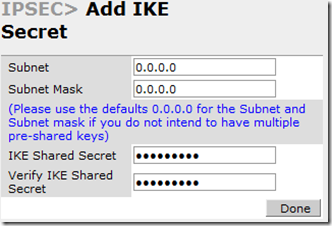
Click “Apply” in the lower right.
Step Four, navigate to Configuration –> Security –> Authentication to setup an internal user. Click on Internal DB on the left. Now you will see a section titled “Users” You want to add one. Click “Add User”. It will auto generate a username and password for you, but you will probably want to change to something more meaningful. 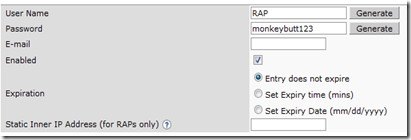 You can leave the rest of the fields blank and click “Apply”.
You can leave the rest of the fields blank and click “Apply”.
Step Five. You are now ready to deploy the AP using the profile you created in step 2 and the VPN information you created in steps Three and Four. Navigate to Configuration –> Wireless –> AP Installation. Click the AP you wish to deploy as a remote AP and click “Provision”.
Now, in the AP Group filed, select from the dropdown, the AP group you set up in step Two.
In the Authentication Method section, select that you will be deploying a Remote AP by clicking the “Yes” radio button. When you do, it will allow you to fill in the IKE PSK and your user credentials you created in step Four. Make sure to uncheck the “Use Automatic Generation” box or you won’t be able to enter your username and password. 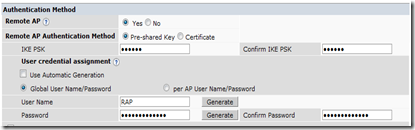
After you have that info entered, you can move on down to select the campus this AP will be deployed to (there is documentation on how to set these up in the user guide). Then, name it something meaningful, and click the “Apply and Reboot” button. The reboot will take a few minutes because that AP will get a new image pushed out to it. 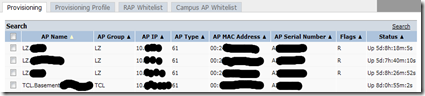 If you have done things right, you should see your new AP’s deployed and in the correct group, and have an “R” in the flag section signifying that it is a “Remote Access Point”. I’ve blotted out the IP address for the remote AP, but it will be something in the range that you setup in Step Two.
If you have done things right, you should see your new AP’s deployed and in the correct group, and have an “R” in the flag section signifying that it is a “Remote Access Point”. I’ve blotted out the IP address for the remote AP, but it will be something in the range that you setup in Step Two.
Well I hope this helps someone out there who is struggling though getting some remote access points up with their Aruba gear. This is the first enterprise class wireless system I have worked with and for the most part, it is a pretty good system. There are ones out there that make it a whole lot easier to do some of these more advanced features though.
How to deploy an Aruba Remote Access Point (RAP) Part 1
At The Chapel we put in an Aruba Wireless system last year (Aruba 650). It was a huge improvement to what we had which was a combination of Linksys and 3Com gear. We are now able to provide public and private wireless networks with just one wireless network. The enhanced management features you get with a controller based system are also huge time savers such as central updates, ability to find the number of clients on the network, and locate those clients in the building.
Well,since we liked the system and it was working for us we decided to put some access points out at our new Lake Zurich campus which didn’t have any wireless. It was easy enough to get things going, just plug the AP into the network, find it on the controller, and deploy it. Done.
Well, not quite. The Aruba system by default wants to set the AP’s up to tunnel back to the controller. This is part of what makes this system so easy to deploy. You don’t have to worry about what vlan the AP’s are on or what their IP address is. The tunnel sends all traffic back to the controller to be routed. The issue is when you have a local resource like a file server, printer, or even local internet connection, all your traffic goes back to the controller and then back to the local network.
We had a local Comcast internet connection at Lake Zurich we wanted to use without tunneling through two other campuses to get to the controller. Luckily, Aruba had a “Remote Access Point” license that was supposed to make deploying our AP-61’s easy. The key words are “supposed to”.
Aruba fails in the documentation department miserably for this RAP feature. I found out though my CDW rep that I could use my AP-61’s if I got an RAP license for each of them. (This is kind of expensive but now it is included free in the Aruba OS 5 release) Next came configuring them. I tried following the documentation but it was all based on older versions of the software and kept referencing setting up firewall rules that are only available in their PEF license which I didn’t have. They also didn’t have an example that matched my scenario of having everything on a private network. All the examples talked about using the VPN feature because you are going across the internet. I upgraded to the Aruba OS 5 which had a wizard to deploy remote AP’s but it didn’t work either.
So I tried and failed again and again. I even sent some bad configs to my AP’s that bricked them! After looking for the reset button I found out my AP’s didn’t have any! Stupid! After some research, I found out that I needed a special “Serial Over Ethernet (SoE) cable” as Aruba calls it and it had a schematic of how to make one. I gave it a try twice and couldn’t get it to work. I then had to fork out about $100 to get one from Aruba! Anyhow, they were back up and running finally but I still didn’t have the RAP feature that I wanted and paid for.
So I called up support again and got someone who seemed to kind of know what I was trying to accomplish. We did a WebEx session and were able to get things going. Because this is getting to be a long post, I’ll show how to set this up in part 2.