Recently, we expanded Public Wireless to all our campuses. We really hammer our network on the weekend when we push video across it and I didn’t want public Wi-Fi traffic to become a problem. We have some access lists on our Cisco routers that do so time-of-day/week bandwidth throttling but it was kind of a pain to set up. So, I decided to see what I could do at the source. I was surprised at how easy it was to implement Bandwidth Management on our public wireless using our SonicWall NSA 240. Here’s how I did it. Your mileage may vary.
Step one. Log into your SonicWall. I know, it’s a big step. Step Two. Navigate to Network –> Address Objects and create an “Object” to match your Public Wireless Traffic. Click “Add…” under Address Objects.
Step Two. Navigate to Network –> Address Objects and create an “Object” to match your Public Wireless Traffic. Click “Add…” under Address Objects. 
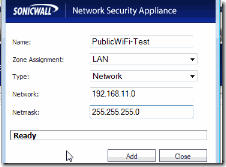
I created an object called “PublicWiFi-Test” for this example and matched it to traffic on network 192.168.11.0/24 which is the IP address range of our Public Wi-Fi traffic. You can match to a number of other identifiers as well.
 Step Three. Navigate to Firewall –> Access Rules. Change the view style to “All Rules” and then click “Add”.
Step Three. Navigate to Firewall –> Access Rules. Change the view style to “All Rules” and then click “Add”. 
Now is when we actually tell the SonicWall what we want to do with the Public Wireless Traffic. In the window that comes up fill out the fields like I have below. What we are doing is telling the firewall to process traffic that is from the LAN to the WAN, from any Service, matching the PublicWiFi-Test object that we defined earlier, to any destination.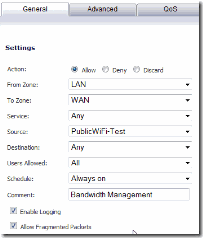 On the “Advanced” tab, leave everything as the default, but check the “Create a reflexive rule” so that inbound traffic will be matched as well.
On the “Advanced” tab, leave everything as the default, but check the “Create a reflexive rule” so that inbound traffic will be matched as well. 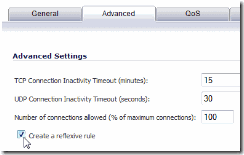 On the QoS tab, change the DSCP Marking Action to “Explicit”. Then change the “Explicit DSCP Value” to “0 – Best effort/Default”. That way, if you have some other policies downstream that mark or generate traffic with a higher DSCP (like video) the PublicWiFi traffic won’t mess with your video feed.
On the QoS tab, change the DSCP Marking Action to “Explicit”. Then change the “Explicit DSCP Value” to “0 – Best effort/Default”. That way, if you have some other policies downstream that mark or generate traffic with a higher DSCP (like video) the PublicWiFi traffic won’t mess with your video feed. 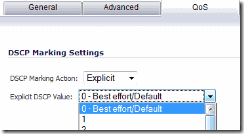
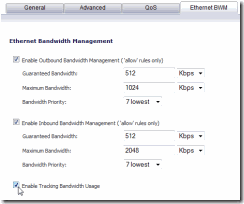
Now, on the Ethernet BWM tab, you will actually configure the Bandwidth Management. Check the first box and then enter a percent or Kbps value for the Guaranteed bandwidth and the Maximum Bandwidth. This first section will apply your settings to “Outbound” traffic or in Internet terms, Upload Speed. One MB should be a good cap. You can also set the “Bandwidth Priority” to 7 which is the lowest. I’m not sure which takes precedence since you already set a value in the QoS tab. Now, click the next box and set the download values. At the bottom you can check the “Enable Tracking Bandwidth Usage” if it makes you happy. Click OK and your ready to go!
 Step Four. You can now test your new policy out by going to a site like http://www.speakeasy.net/speedtest/ If you’ve done it right, your upload and download numbers should match the numbers you set in your policy. On my first try I had the values reversed.
Step Four. You can now test your new policy out by going to a site like http://www.speakeasy.net/speedtest/ If you’ve done it right, your upload and download numbers should match the numbers you set in your policy. On my first try I had the values reversed.
So, that was easier than I thought it was going to be. I took it one step further because we have multiple campuses with different IP schemas right now for wireless. I created more address objects and added them to an Address Group. I then changed the setting in my policy to reference the Address Group instead of the single Address Object. The issue I see with this is that all traffic that matches these limits will share that bandwidth cap. So, if I have 4 public clients, their bandwidth would be (2048 Kbps / 4) or 512 Kbps. I’ll have to play around with things and see how it goes. You can set the policy to a schedule so I might just have it be active on the weekends.
I hope this helps someone. If it does or you have questions, leave a comment.
10 comments:
This is great stuff. It kinda falls apart when doing multi-WAN on the Sonicwall, though. You have to make sure your fastest interface is on X1, as the BWM parameters on that interface are the ones it cares about when setting traffic management policy. I'm not even entirely sure it can handle BWM properly on WAN interfaces other than the primary.
What we've done for an upcoming conference is create a separate guest interface and subnet for our conference presenters, given them their own private SSID on the Ruckus system with a guest pass, and then set the NAT/routing for that subnet to go out one of the DSL interfaces, and then removed that interface from the WAN load balance pool. It's not perfect, but it does give the presenters internet capacity that is unimpeded by the nearly 2000 guests we'll have at the conference.
Thanks for the feedback Ian! If I ever do dual ISP's on my firewall, I know what I'll have to change!
you let me know more ,thanks!
thanks for the help Jeremy. Works like a charm!
Can this be done with VOIP server on the LAN? I need to prioritize RTP traffic from Asterisk Server located on the LAN. I'm using single T1 from the WAN side.
thanks.
Here is how Sonicwall handles BWM with WAN load balancing:
a) If two interfaces are configured as WAN and load balancing is NOT enabled, apply BWM only to the primary WAN interface.
b) If two interfaces are configured as WAN and load balancing is enabled
- For Active\Passive Failover, BWM is done only on the active WAN interface.
- For Round Robin and Ratio options, link capacity is the sum of available BW for primary and secondary WAN interface and BWM is done on both interfaces.
- For Spill Over option, link capacity is Primary’s available BW and BWM is done on primary interface before the spill over occurs. And after the spill over occurs, secondary interface’s capacity is used and BWM is done on the secondary WAN interface.
The complete guide is here:
https://www.fuzeqna.com/sonicwallkb/consumer/kbdetail.asp?kbid=8345&p=t
Or if the link is dead, the heading is:
UTM: Bandwidth Throttling of Online Streaming Video Using Application Firewall.
Note: Some of the terms may vary for each firewall
Is this on a per user basis or total subnet?
Great article!
Please i want to know if this can be done on a per user basis. I am asking because I manage a network at a research institute and I noticed that one user hammers the network anytime he is on. I want to assign a BW to him alone or filter his IP from accessing the internet. I am using a sonicwall nsa 240 bridged to 2901 cisco router
You can set a single IP QoS rule, and cap his bw.
Post a Comment